How to setup Metasploitable 3 on Windows 10
How to setup Metasploitable 3
Are you installing Metasploitable 3 on a VM that is running on VMware ESXi like us? Don’t forget to enable ‘Hardware virtualization’ for the VM CPU.
Before we can build the VM we have to install Vagrant and Virtualbox using the downloaded installation files. We will not demonstrate the installation procedure for this software as it’s very straightforward and only involves clicking ‘next’ a couple times. Next we need to install the Vagrant reload plugin and we need to download Packer.
Install Vagrant reload plugin
Change the directory on the command line to the directory where you have downloaded and unpacked the Vagrant Reload plugin. Then run the following command to install the plugin:
vagrant plugin install vagrant-reload
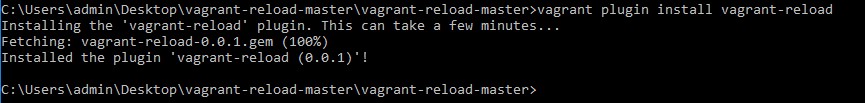
Vagrant plugin vagrant-reload successfully installed.
Download Packer
The next step is to download Packer from the following download page:
https://www.packer.io/downloads.html
Creating the Metasploitable 3 VM
Now that we have all pre-requisites installed we can use Packer to setup the Virtual Machine in Virtualbox. Move the command line to the Metasploitable 3 location and run the following command from an elevated command line:
packer build windows_2008_r2.json
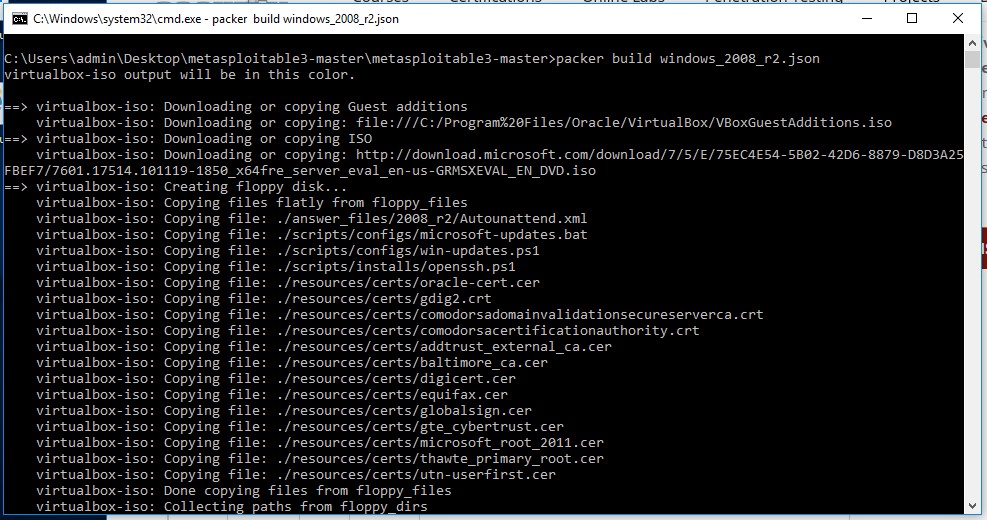
Building the Metasploitable 3 VM will take a while.
This command will take a while to complete because first it will download a Windows 2008 evaluation copy from the Microsoft website. When the download is finished, the script will continue to setup the virtual machine in Virtualbox and install Windows 2008 on the virtual machine. The entire process will take anywhere from 30-60 minutes. This depends on the configuration of your host machine and the speed of your internet connection. When the script is finished the output looks as following:
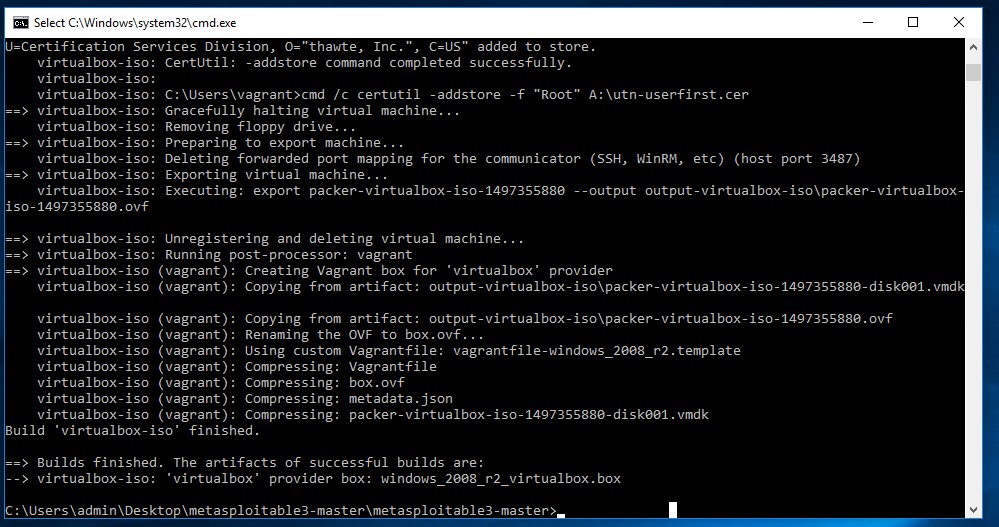
Metasploitable 3 build process finished without errors.
When the script is finished run the following command:
vagrant box add windows_2008_r2_virtualbox.box –name=metasploitable3
Note: Use 2 dashes for the name parameter here.
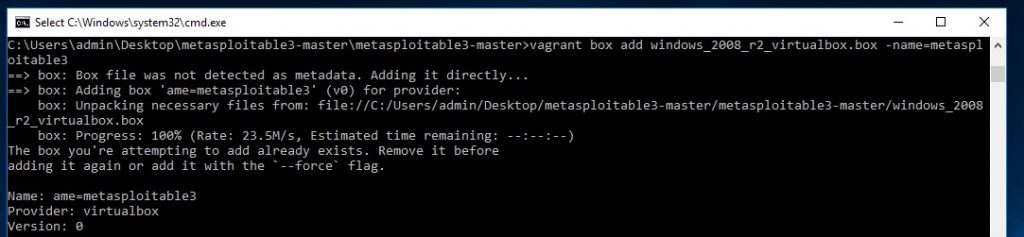
Metasploitable 3 added to the Vagrant environment.
Finally we have to run the one more command to have Vagrant execute the scripts that install the vulnerable software on the Windows server 2008 virtual machine. Run the following command and expect to wait another 15-30 minutes until completion:
vagrant up
This will conclude the installation of Metasploitable 3 and you should be able to start the VM within Virtualbox.
Metasploitable 3 installation errors with Vagrant
The Metasploitable 3 setup process is a bit tricky and prone to errors related to specific versions of the prerequisites. Most errors I faced while writing this tutorial were avoided by using the versions of Vagrant, Packer & Virtualbox mentioned earlier in this tutorial. Especially the latest version of Virtualbox resulted in many errors after issuing the vagrant up command.
Another error that may occur during the installation of vulnerable software is the following: “chocolatey is not recognized as an internal or external command”. The error didn’t only apply to Chocolatey but also some other scripts. To get rid of this error I’ve added the following directory to the Path variable:
C:\Users\admin\Desktop\metasploitable-3-master\metasploitable-3-master\scripts\installs\
Running Kali Linux VM on the same host
If you’re running your Kali Linux virtual machine in Virtualbox on the same host you have to make sure that you set the correct network settings. Otherwise you won’t be able to connect to the Metasploitable 3 machine from your Kali Linux attack box. You’re not required to alter the network settings for the Metasploitable 3 machine, only for the Kali Linux VM:
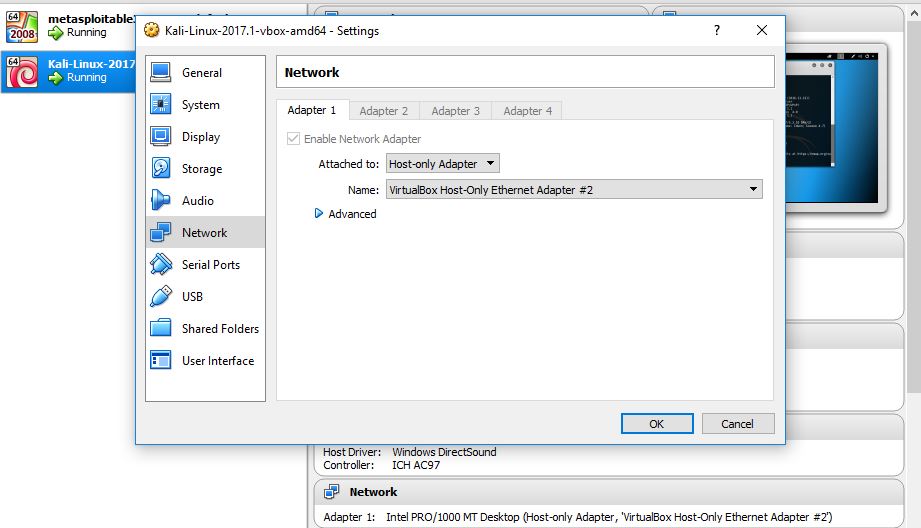
Choose: Host-only adapter.
Now that we’ve completed the installation procedure for Metasploitable 2 we are ready to boot in in Virtualbox. The default username for the virtual machine is “vagrant” with password “vagrant”. Even though the installation process produced quiet some errors there were none that we couldn’t fix quickly (Google is your friend!). I must say that the developers of Metasploitable 3 did a great job on the installation procedure and providing a vulnerable Windows machine to the public.
You can also buy instant:


Cashapp Money Transfer Click here
Paypal Money Transfer Click here
Western Union Money Transfer Click here
Venmo Money Transfer Click here
Bank Money Transfer Click here to Contact Us
